In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount. Among the most concerning vulnerabilities are zero-day exploits, which can wreak havoc on systems and data. In this comprehensive guide, we delve deep into the world of zero-day exploits, offering valuable insights, expert analysis, and actionable advice to help you understand, mitigate, and protect your digital assets.
Understanding Zero-Day Exploits
What Are Zero-Day Exploits?
Zero-day exploits are a type of cyber attack that targets vulnerabilities in software or hardware that are unknown to the vendor, hence the term “zero-day.” These attacks occur on the same day that the vulnerability is discovered by malicious actors, leaving no time for developers to release patches or fixes. This makes zero-day exploits particularly dangerous, as they can be unleashed without warning, potentially causing significant damage.
How Do Zero-Day Exploits Work?
Zero-day exploits typically follow a sequence of events:
- Discovery: The attacker identifies a vulnerability in a software application, operating system, or hardware component.
- Exploitation: The attacker creates a malicious code or payload that takes advantage of the vulnerability to gain unauthorized access or control over the targeted system.
- Delivery: The attacker deploys the exploit, often through email attachments, infected websites, or other means.
- Execution: Once the exploit is executed, it can lead to data breaches, system crashes, or other malicious activities.
The Impact of Zero-Day Exploits
Zero-day exploits can have severe consequences for individuals, businesses, and even governments. Some of the potential impacts include:
Data Breaches
Zero-day exploits can lead to unauthorized access to sensitive data, such as personal information, financial records, or intellectual property. This breach of confidentiality can result in financial losses and damage to an organization’s reputation.
System Compromise
When a zero-day exploit is successfully executed, the attacker gains control over the targeted system. This can lead to data manipulation, software malfunctions, and even a complete system takeover.
Financial Losses
Remediating the damage caused by a zero-day exploit can be costly. Businesses may incur expenses related to incident response, legal fees, and regulatory fines.
Protecting Against Zero-Day Exploits
Stay Informed
To defend against zero-day exploits, it’s crucial to stay informed about the latest vulnerabilities and security updates. Subscribing to security newsletters, following industry blogs, and monitoring vendor advisories can help you keep abreast of emerging threats.
Implement Strong Security Measures
Prevention is key. Employ robust cybersecurity measures, including firewalls, intrusion detection systems, and antivirus software. Regularly update and patch your systems to address known vulnerabilities.
Employee Training
Human error is often a weak point in cybersecurity. Ensure that your employees are well-trained in recognizing phishing attempts and other social engineering tactics that can lead to zero-day exploits.
Zero-Day Vulnerability Disclosure Programs
Some organizations offer bug bounty programs, encouraging ethical hackers to discover and report vulnerabilities before malicious actors can exploit them. Participating in these programs can enhance your security posture.
Zero-day vulnerabilities represent undiscovered security weaknesses within IT systems. When threat actors uncover these vulnerabilities before anyone else does, they gain the potential to exploit the system. This exploitation may involve actions such as gaining unauthorized access, executing code, stealing data, or taking remote control, among others.
Regrettably, victims of such breaches find themselves in a precarious situation, as there is no immediate remedy available. They remain vulnerable until a patch becomes accessible, a process that can span from a few days to several months, leaving them exposed to potential cyber threats and attacks.
What Is a Zero-Day Exploit?
Understanding Zero-Day Exploits: Clarifying the Terminology
The term “zero-day exploit” carries a significant weight in the realm of cybersecurity, often shrouded in confusion. Let’s unravel this complexity and shed light on the distinct roles played by zero-day vulnerabilities, zero-day exploits, and zero-day attacks:
- Zero-Day Vulnerabilities: These are security flaws lurking in software, hardware, or firmware, discovered by individuals outside the purview of the responsible software vendor. They exist in a state of obscurity until the vendor becomes aware of the issue.
- Zero-Day Exploits: A zero-day exploit is a precise technique or strategy employed by hackers to capitalize on a zero-day vulnerability. It’s the means by which threat actors compromise an IT system.
- Zero-Day Attacks: These are cyber assaults orchestrated around a zero-day exploit. They rely on the exploit’s power to infiltrate and harm the target system.
A zero-day exploit typically serves as a stepping stone for hackers, granting them unauthorized access or control over a system. Once this foothold is established, the malefactors can proceed with their ultimate objectives, such as data theft, ransomware deployment, or advanced persistent threats (APTs).
It’s worth noting that approximately 75% of zero-day exploits hinge on memory corruption issues, facilitating actions like buffer overflows or out-of-bounds read/write operations. Meanwhile, logic and design flaws, allowing for sandbox escapes and remote privilege escalations, account for the second most prevalent cause (around 14%).
In an ideal scenario, the individual who uncovers a zero-day vulnerability acts as an ethical hacker, promptly notifying the software vendor. The vendor, armed with this knowledge, undertakes code rectification and disseminates a patch. It’s imperative for users to expeditiously update their systems with the provided patch to thwart potential threats. Unfortunately, a substantial portion of users neglect this crucial step, enabling cybercriminals to persistently employ the same exploit even after the vendor has supplied a remedy.

What Is the Best Example of a Zero-Day Exploit?
Here are some notable instances of devastating zero-day exploits from recent years:
- WhatsApp (2019): In 2019, hackers exploited a vulnerability in WhatsApp’s voice call feature to implant spyware on user devices. This led to the compromise of thousands of devices, allowing attackers to eavesdrop on calls and messages.
- ZOOM (2020): In 2020, threat actors uncovered a vulnerability in ZOOM, which granted them remote access to the PCs of users running older versions of Windows.
- Microsoft ATM Library (March 2020): Microsoft alerted its users to two zero-day exploits in the built-in Adobe Type Manager (ATM) library. These exploits targeted remote code execution (RCE) flaws, enabling attackers to execute scripts and infect vulnerable devices.
- Sophos PostgreSQL Database (April 2020): Criminals exploited an SQL injection vulnerability to target Sophos’ built-in PostgreSQL database server. They used this flaw to inject code into the database, alter security settings, and install malware.
- iMessage (Late 2020): In late 2020, threat actors leveraged a vulnerability in iMessage to deploy the Pegasus spyware through a zero-click attack, requiring no action from the victim. This malware provided hackers with remote access to iOS devices, enabling data theft and call interception.
- LinkedIn (April 2021): In April 2021, LinkedIn discovered that threat actors had compromised over 700 million user accounts via a zero-day exploit. Hackers scraped data from an archive containing public information (names, email addresses, phone numbers, job titles, etc.) and sold this data on the Dark Web for use in spamming or phishing campaigns.
- Microsoft Netlogon Protocol (August 2021): In August 2021, Microsoft urgently advised users to install a security update addressing a vulnerability in the Netlogon protocol. This zero-day exploit allowed hackers to acquire domain admin privileges.
These instances underscore the ongoing challenges posed by zero-day exploits and the critical importance of prompt detection and mitigation in the ever-evolving landscape of cybersecurity.
How Does a Zero-Day Exploit Work?
A zero-day exploit is a type of cyber attack that takes advantage of a previously unknown vulnerability in software or hardware. These exploits are called “zero-day” because they occur on the same day that the vulnerability is discovered, leaving zero days for the software or hardware vendor to fix or patch the issue. Here’s how a zero-day exploit typically works:
- Discovery of Vulnerability: The first step in a zero-day exploit involves the discovery of a vulnerability in a software application, operating system, or hardware component. This vulnerability is essentially a weakness or flaw in the system’s code that can be exploited by an attacker.
- Exploitation: Once the attacker identifies the vulnerability, they create a piece of malicious code or a software tool, often called an “exploit,” specifically designed to take advantage of this weakness. The exploit is crafted to trigger the vulnerability and gain unauthorized access or control over the targeted system.
- Delivery: The attacker needs a way to deliver the exploit to the target system. This can be done through various means, such as email attachments, infected websites, malicious links, or even physical access to the device in some cases. The goal is to trick the user or system into executing the exploit unknowingly.
- Execution: When the exploit is executed on the target system, it takes advantage of the vulnerability to achieve the attacker’s goals. This may involve stealing sensitive data, compromising system security, or performing other malicious activities. The attacker can gain control over the system, manipulate data, or even install additional malware.
- Concealment: To avoid detection and maintain access to the compromised system, the attacker may employ various techniques to conceal their presence. This could include erasing logs, using encryption, or employing rootkit tools to hide malicious processes.
- Potential Damage: Depending on the attacker’s intentions, the consequences of a successful zero-day exploit can vary. It could lead to data breaches, system crashes, unauthorized access, or other forms of damage to the targeted system or network.
- Zero-Day Status: The term “zero-day” indicates that, at the time of the attack, the software or hardware vendor is unaware of the vulnerability. This lack of awareness means there are no available patches or updates to fix the issue, making it extremely challenging for organizations to defend against the exploit.
It’s worth noting that zero-day exploits are highly valuable in the cybercriminal underground and are often used sparingly to maximize their effectiveness. To protect against zero-day exploits, organizations need to implement robust cybersecurity measures, stay informed about emerging threats, and follow best practices for secure computing.
The Genesis of Zero-Day Exploits: From Discovery to Exploitation
Zero-day exploits invariably commence with the identification of an exploitable flaw, a pivotal starting point. Threat actors employ two prevalent methods to unearth these vulnerabilities:
- Active Exploration: Threat actors interact with and experiment on various applications, probing for weaknesses.
- Dark Web Acquisition: Alternatively, they may acquire information on vulnerabilities from illicit sources on the Dark Web.
Upon uncovering a vulnerability, hackers set out to determine how best to exploit it, often involving the development of malware. To validate the efficacy of the zero-day exploit, hackers frequently execute proof-of-concept trials.
With the exploit in hand, the attackers must decide on their next course of action. They generally pursue one of two strategies, contingent on the nature of the exploit:
- Targeted Attacks: In cases where hackers wish to specifically target a particular organization or individual, they tailor their approach accordingly.
- Non-Targeted Attacks: Conversely, if the goal is to infect as many systems as possible, criminals may employ bots and automated scanners to identify vulnerable victims en masse.
The subsequent phase involves infiltrating the targeted devices. Unless the zero-day flaw inherently provides access, hackers resort to conventional infection methods, such as:
- Deceptive email attachments.
- Malicious websites designed for drive-by downloads.
- Malvertising campaigns.
- Direct network assaults.
Once inside the system, the zero-day vulnerability furnishes the means to carry out a range of malicious activities, including:
- Remote Code Execution (RCE).
- Injection of malevolent code.
- Privilege escalation.
- Circumvention of authentication mechanisms.
- Extraction of sensitive data (e.g., login credentials, financial information, intellectual property).
- Eavesdropping on network traffic.
- Manipulation of network infrastructure.
- Establishment of persistent access points and backdoors.
- Seizure of remote control.
The attacker persists in exploiting the vulnerability until their activities are detected and reported, compelling the vendor to patch the flaw and disseminate an update. The duration of this cycle varies considerably, contingent on the complexity of the issue, but the average timeframe spans around 97 days.
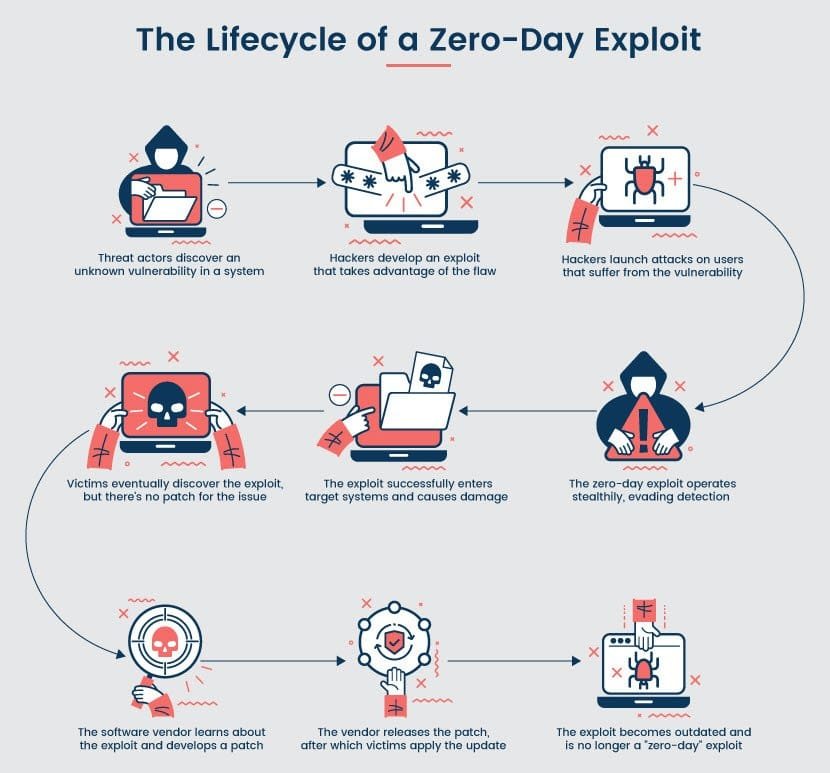
Who Are Zero-Day Exploit Attackers?
Zero-day exploit attackers, often referred to as “threat actors,” come from diverse backgrounds and motivations. These individuals or groups exploit zero-day vulnerabilities for various purposes, which can range from financial gain to political or ideological reasons. Here’s an overview of the different types of zero-day exploit attackers:
- Criminal Hackers: Some zero-day exploit attackers are motivated by financial gain. They may use these exploits to steal sensitive personal information, and credit card data, or conduct ransomware attacks. Criminal hackers often seek financial rewards and may sell stolen data on the black market or demand ransom payments.
- State-Sponsored Actors: Governments and intelligence agencies are known to employ zero-day exploits for espionage, cyber-espionage, and national security purposes. State-sponsored attackers may use zero days to gain access to the computer systems of foreign governments, military organizations, or critical infrastructure facilities.
- Hacktivists: Hacktivist groups or individuals use zero-day exploits to advance a political or ideological agenda. They may target government websites, corporations, or organizations that they perceive as oppressive or against their beliefs. The goal is often to disrupt operations, steal sensitive information, or deface websites to convey a message.
- Cyberterrorists: In rare cases, individuals or groups with extreme ideologies may use zero-day exploits to carry out acts of cyberterrorism. Their aim is to create fear, disrupt society, or cause harm through cyberattacks on critical infrastructure, such as power grids, transportation systems, or financial institutions.
- Security Researchers: Not all zero-day exploit attackers have malicious intent. Some are cybersecurity researchers who discover and responsibly disclose vulnerabilities to software vendors. However, there have been cases where these researchers have been mistakenly labeled as attackers when their intentions were purely to improve security.
- Cybercriminal Organizations: Organized cybercriminal groups may use zero-day exploits as part of their operations. These groups often have the resources and expertise to discover or purchase zero-days and use them to conduct sophisticated attacks, including data breaches and financial fraud.
- Script Kiddies: Inexperienced individuals, often referred to as “script kiddies,” may dabble in hacking and use publicly available zero-day exploits without fully understanding the technical aspects. Their motivations can vary, from seeking notoriety to causing chaos for amusement.
It’s important to note that zero-day exploit attackers can be highly skilled and difficult to track. The motivations behind their actions can range from financial gain to political activism or even ideological extremism. To defend against these attackers, organizations must implement robust cybersecurity measures, regularly update and patch their systems, and stay vigilant for signs of intrusion or compromise. Additionally, responsible disclosure practices by security researchers can help reduce the impact of zero-day exploits by facilitating timely fixes from software vendors.
Unmasking the Culprits Behind Zero-Day Exploits: The Elusive Hunt for Attribution
Attributing zero-day exploits to their perpetrators poses a formidable challenge, as attackers employ various techniques to cloak their identities. These evasion tactics include:
- Routing through Compromised Systems: Attackers often route their activities through multiple compromised systems, obscuring their origin.
- Encryption Strategies: The use of diverse encryption techniques adds an additional layer of anonymity to their actions.
- Anonymization Services: Attackers may leverage anonymization services to further obfuscate their digital footprints.
Remarkably, a significant portion, over 40%, of zero-day exploits identified in the years 2020, 2021, and 2022 remain unattributed and unclaimed. These elusive actors can be categorized into several groups:
- Cybercriminal Entities: These include both individuals and groups motivated primarily by financial gain. They may either breach targets directly or profit by selling their exploits to other malicious actors.
- Nation-States and Private Intelligence Agencies: Some zero-day exploit developers serve the interests of nation-states or private intelligence agencies. Their exploits are often crafted for purposes of espionage, surveillance, or offensive cyber operations.
- Hacktivism Groups: Hacktivist organizations employ zero-day exploits to infiltrate computer systems in pursuit of social or political causes. Their motivations extend beyond financial gain, focusing on advocacy and activism.
- Cybersecurity Researchers: In some cases, even cybersecurity researchers become part of the equation. These individuals may test exploits without proper authorization or engage in such activities for personal gain.
The labyrinthine world of zero-day exploit attribution continues to perplex cybersecurity experts, highlighting the persistent need for advanced techniques and international collaboration to unmask those responsible for these covert and potentially harmful actions.
Who Are the Targets of Zero-Day Exploit Attacks?
The targets of zero-day exploit attacks can be anyone who uses the software that has the vulnerability, such as individuals, businesses, governments, or even critical infrastructure
The All-Encompassing Reach of Zero-Day Exploits: Vulnerabilities and Targets
Zero-day exploits cast a wide net, exploiting vulnerabilities across diverse systems, including:
- Operating systems.
- Web browsers.
- Office applications.
- Network protocols.
- Open-source and commercial software tools.
- Anti-virus and malware detection tools.
- Hardware and firmware.
- Hardware components.
- Internet of Things (IoT) devices.
The inherent danger lies in the fact that anyone using these technologies, particularly those connected to the Internet, stands as a potential victim. Zero-day exploits exhibit two overarching approaches:
- Targeted Zero-Day Attacks: These pinpoint potentially lucrative targets, encompassing small to medium-sized businesses (SMBs), large corporations, government agencies, high-profile individuals, healthcare organizations, and technology firms, among others.
- Non-Targeted Attacks: In contrast, non-targeted campaigns cast a wider net, seeking out any device harboring a vulnerability. These endeavors serve dual purposes: harvesting personal information, such as passwords, credit card details, or healthcare data, and commandeering devices to amass a botnet for distributed denial-of-service (DDoS) attacks.
The pervasive nature of zero-day exploits underscores the critical importance of robust cybersecurity measures for both individuals and organizations, as the threat landscape encompasses a vast array of potential targets.
How Common Are Zero Day Exploits?
Zero-day exploits are relatively rare compared to exploits of known vulnerabilities, but they are still very common and dangerous. In 2022, threat actors discovered and leveraged a total of 55 zero-day vulnerabilities. In 2021, at least 66 zero-day exploits were found in use, breaking the record for the most zero-day attacks in a year. Zero-day attacks can target any software, such as Adobe Flash, Microsoft Windows, or Java.
Assessing the Prevalence of Active Zero-Day Exploits: An Elusive Endeavor
Determining the exact count of active zero-day exploits presents an insurmountable challenge, primarily due to their very essence—they rely on undisclosed vulnerabilities. However, there is a consensus among cybersecurity experts that zero-day exploits are relatively scarce when compared to the exploitation of known vulnerabilities.
In the year 2022, threat actors succeeded in identifying and employing a total of 55 zero-day vulnerabilities. Of these, 53 facilitated the elevation of privileges or remote code execution by hackers. This number represents a decline compared to the preceding year, 2021, which witnessed the discovery of at least 66 distinct zero-day exploits. Nonetheless, it is essential to note that the overall frequency of zero-day attacks continues to trend upwards, underscoring the persistent and evolving nature of this cybersecurity challenge.
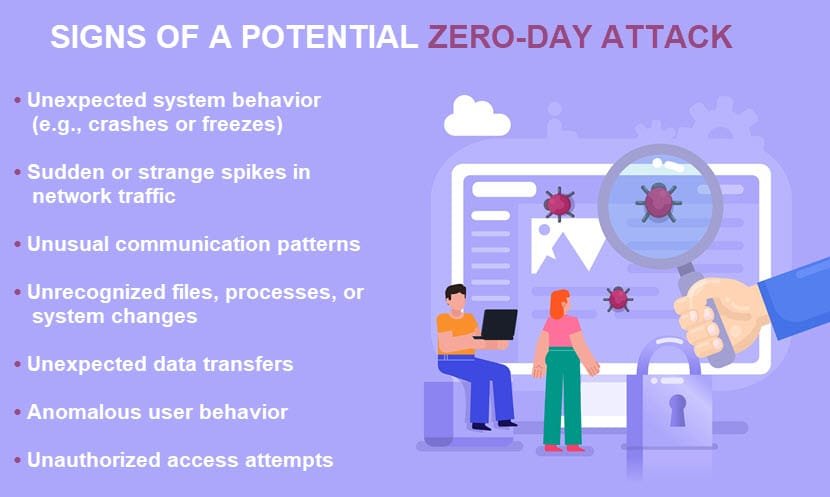
How to Detect Zero-Day Exploit Attacks?
Detecting zero-day exploit attacks is a significant challenge because these attacks target vulnerabilities that are unknown to software vendors and, therefore, lack available patches or signatures for detection. However, while it’s challenging, it’s not impossible. Detecting zero-day exploit attacks requires a combination of proactive security measures and vigilant monitoring. Here are some strategies and techniques that can help in the detection of zero-day exploit attacks:
- Behavioral Analysis:
- Implement advanced threat detection solutions that use behavioral analysis to identify unusual patterns or behaviors in network traffic and system activities.
- Look for anomalies in system processes, file operations, or network communications. Unusual behaviors may indicate an attack.
- Heuristic Analysis:
- Use heuristic analysis to detect suspicious files or code that exhibit characteristics commonly associated with malicious activity.
- Monitor for unexpected code execution, privilege escalation, or changes to system configurations that may suggest an exploit attempt.
- Network Traffic Analysis:
- Employ intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor network traffic for known attack patterns.
- Look for unusual data flows or communication patterns that may indicate a zero-day exploit attempt.
- Endpoint Protection:
- Utilize advanced endpoint protection solutions that can detect and block malicious processes or files based on their behavior, rather than relying solely on signatures.
- Monitor for unauthorized access attempts or unusual user behavior on endpoints.
- Sandboxing:
- Implement sandboxing technology to isolate and analyze suspicious files or code in a controlled environment. Sandboxing can help identify zero-day exploits by observing their behavior without exposing the network or endpoints to risk.
- Threat Intelligence Feeds:
- Subscribe to threat intelligence feeds that provide information about emerging threats and vulnerabilities. These feeds may include indicators of compromise (IoCs) associated with zero-day exploits.
- User and Entity Behavior Analytics (UEBA):
- UEBA solutions can help detect anomalies in user and entity behavior, such as unusual login patterns or access to sensitive resources, which may be indicative of an attack.
- Zero-Day Vulnerability Scanning:
- Regularly scan your network and systems for known vulnerabilities. While this won’t detect zero-day exploits directly, it can help identify potential entry points that attackers might target.
- Incident Response Plans:
- Develop and regularly update incident response plans that outline how to respond to a suspected zero-day exploit or any other security incident. Having a well-defined plan in place can help minimize the impact of an attack.
- User Awareness and Training:
- Educate users about security best practices, including recognizing phishing attempts and suspicious emails. Users can often be the first line of defense against social engineering tactics used in zero-day attacks.
- Continuous Monitoring:
- Implement continuous monitoring of network and system activities to detect any signs of unusual or unauthorized behavior in real time.
- Collaboration and Information Sharing:
- Collaborate with industry peers and share threat information through Information Sharing and Analysis Centers (ISACs) or similar organizations. Collective intelligence can help in early detection.
While it’s impossible to guarantee 100% detection of zero-day exploit attacks, a combination of these strategies and technologies can significantly improve your organization’s ability to identify and respond to such threats. Proactive security measures, ongoing monitoring, and a well-prepared incident response plan are essential components of a comprehensive security strategy.
The Elusive Nature of Zero-Day Exploits: Detecting the Undetectable
Zero-day exploits pose a formidable challenge for standard anti-malware software and firewalls due to their lack of known signatures or recognizable patterns. To enhance the detection of these insidious threats, companies employ a multifaceted approach, relying on behavior analytics. Here’s how organizations increase their odds of identifying zero-day exploits:
- Enhanced Network Monitoring: Companies bolster their network monitoring capabilities with tools designed to scrutinize network traffic and behavior for irregularities and suspicious activities. The use of an Intrusion Detection System (IDS) aids in pinpointing unusual network patterns and unexpected data traffic.
- Behavior-Based Analysis: Behavior-based analysis tools come into play, monitoring system processes, user behavior, and application activities. These tools establish a baseline of normal behavior and promptly flag any deviations from this established norm.
- Endpoint Security Improvement: Endpoint security is fortified through the adoption of tools employing behavior-based analysis, machine learning (ML), and artificial intelligence (AI). These tools are instrumental in detecting and halting malicious activities on endpoints.
- Attack Surface Management (ASM): The deployment of an attack surface management tool takes center stage. ASM tools continually surveil the attack surface, identifying unauthorized assets such as shadow IT devices or rogue cloud instances.
- Employee Training: An educated workforce plays a pivotal role in zero-day exploit detection. Companies invest in employee training to heighten awareness of zero-day threats, educate staff about social engineering techniques, and promote safe computing practices.
This multifaceted approach seeks to bridge the gap in detecting zero-day exploits, acknowledging their elusive nature and the evolving tactics of cyber adversaries. By integrating behavior analytics and comprehensive monitoring, organizations strive to fortify their defenses against these stealthy threats.
What Are the Best Defenses Against Zero-Day Exploit Attacks?
Shielding Against Zero-Day Exploits: Essential Defensive Strategies
While the unique nature of zero-day exploits makes guarding against specific exploits challenging, organizations can adopt general measures to reduce their vulnerability. Here’s a comprehensive set of actions to fortify your defenses:
- Patch Promptly: Ensure that all patches are promptly applied across the organization. This minimizes the window of opportunity for attackers to exploit newly discovered vulnerabilities.
- Auto-Update Programs: Configure software programs to auto-update wherever feasible to maintain current defenses.
- Leverage Behavior-Based Analytics: Deploy security tools equipped with behavior-based analytics to detect anomalies and unusual activities on your network.
- Out-of-Date Software Alerts: Set your anti-virus tools to flag out-of-date software, prompting timely updates.
- Source Trustworthiness: Educate employees never to download or install software from untrusted or dubious sources.
- Security Education: Promote security best practices among employees to mitigate the risk of falling victim to social engineering tactics.
- Enhance Wi-Fi Security: Implement robust security schemes like Wi-Fi Protected Access 2 (WPA2) to bolster protection against wireless-based attacks.
- Network Segmentation: Segment your network to restrict an attacker’s lateral movement, preventing access to mission-critical parts of the network.
- Endpoint Security: Deploy endpoint security tools capable of monitoring and automatically responding to anomalous code execution.
- Zero Trust Security: Enforce a zero-trust security model to minimize the potential impact of successful zero-day exploits and limit unauthorized control or access.
- Access Control: Strengthen network access controls to thwart rogue machines from gaining remote entry to critical systems.
- Input Validation: Implement input validation and sanitization to prevent hackers from experimenting with input fields.
- IPsec Encryption: Utilize IPsec (IP security protocol) to enforce in-transit encryption and authentication for network traffic.
- Vulnerability Assessments: Conduct regular vulnerability assessments to unearth exploitable weaknesses.
- Penetration Testing: Consider outsourcing penetration testing services to gauge your system’s resilience against ethical hackers.
- Incident Response Plan: Develop a comprehensive incident response plan to swiftly and effectively address zero-day exploits and cyberattacks.
By proactively implementing these measures, organizations can bolster their defenses and reduce the potential impact of zero-day exploits, contributing to a more resilient and secure digital environment.
Defending against zero-day exploit attacks is a critical aspect of cybersecurity, as these attacks target vulnerabilities that are unknown to vendors, leaving systems vulnerable to exploitation. To protect your organization, consider implementing the following best defenses against zero-day exploit attacks:
- Regular Software Updates and Patch Management:
- Keep all software, operating systems, and applications up to date with the latest security patches. While this won’t prevent all zero-day attacks, it can protect against known vulnerabilities that attackers may exploit.
- Network Segmentation:
- Implement network segmentation to isolate critical systems and limit the lateral movement of attackers within your network. This can prevent an attacker from easily compromising all systems in the event of a successful zero-day attack.
- Application Whitelisting:
- Use application whitelisting to allow only trusted and authorized software to run on your systems. This can prevent the execution of malicious code and unapproved applications.
- Endpoint Protection and EDR Solutions:
- Deploy advanced endpoint protection and Endpoint Detection and Response (EDR) solutions that use behavior-based analysis to detect and respond to suspicious activities and zero-day exploits on endpoints.
- Intrusion Detection and Prevention Systems (IDS/IPS):
- Use IDS and IPS solutions to monitor network traffic for unusual patterns and known attack signatures. These systems can help detect and block zero-day exploit attempts.
- User Education and Awareness:
- Train employees and users to recognize phishing attempts, suspicious emails, and social engineering tactics that may lead to zero-day exploits. User awareness is a crucial line of defense.
- Zero-Day Vulnerability Scanning:
- Regularly scan your network and systems for vulnerabilities, even those not yet known to attackers. Vulnerability scanning tools can help you identify and patch potential entry points.
- Behavioral Analytics:
- Employ behavioral analytics tools to monitor user and entity behavior. Anomalous activities can be early indicators of zero-day attacks.
- Sandboxing and Isolation:
- Use sandboxing technology to isolate and analyze potentially malicious files or code in a controlled environment. Sandboxing can help identify and understand the behavior of zero-day exploits.
- Zero-Day Vulnerability Disclosure Programs:
- Participate in vulnerability disclosure programs or bug bounty programs to encourage ethical hackers to report zero-day vulnerabilities to you before they are exploited by malicious actors.
- Incident Response Planning:
- Develop and regularly update an incident response plan specific to zero-day exploits. Clearly define roles and procedures for responding to such incidents to minimize their impact.
- Threat Intelligence Sharing:
- Collaborate with industry peers and share threat intelligence through Information Sharing and Analysis Centers (ISACs) or other forums. This collective intelligence can provide early warnings of emerging zero-day threats.
- Encryption and Data Protection:
- Encrypt sensitive data to protect it even if an attacker gains access to your systems. Proper data protection can limit the impact of a breach.
- Continuous Monitoring:
- Implement continuous monitoring to detect and respond to unusual or unauthorized activities in real time.
- Security Best Practices:
- Follow industry-standard security best practices, such as the Principle of Least Privilege (PoLP), to limit the access and permissions of users and systems.
- Vendor Relationships:
- Establish strong relationships with software and hardware vendors to quickly receive and apply patches when they become available.
Remember that no defense is foolproof, but a combination of these measures can significantly reduce the risk of falling victim to zero-day exploit attacks. A proactive and layered approach to security is essential to protect your organization’s digital assets.
Conclusion
In an era where cyber threats continue to evolve, understanding zero-day exploits is essential for anyone responsible for safeguarding digital assets. By staying informed, implementing robust security measures, and fostering a security-conscious culture, you can significantly reduce the risk of falling victim to these elusive and damaging attacks.
Remember, cybersecurity is an ongoing process. Continuously assess and enhance your defenses to stay one step ahead of cybercriminals.
